
Serverside template injection Explanation, Discovery, Exploitation - Understanding the mechanisms, risks, and. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. See examples of ssti vulnerabilities,. If an application improperly handles user. You should also read this: Slingshot Templates

Server Side Template Injection Vulnerability Explained TryHackMe SSTI - Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Understanding the mechanisms, risks, and. See examples of ssti vulnerabilities,. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. You should also read this: Christmas Postcard Template

Server Side Template Injection SSTI vulnerability - If an application improperly handles user. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Understanding the mechanisms, risks, and. Find out how to identify, remediate, and prevent this vulnerability with examples and references. See examples of ssti vulnerabilities,. You should also read this: Holiday Hours Template Word
Server Side Template Injection (SSTI) by Eren Sagdic Medium - If an application improperly handles user. Understanding the mechanisms, risks, and. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. See examples of ssti vulnerabilities,. Find out how to identify, remediate, and prevent this vulnerability with examples and references. You should also read this: Free Hair Bow Template
Server Side Template Injection - Understanding the mechanisms, risks, and. Find out how to identify, remediate, and prevent this vulnerability with examples and references. If an application improperly handles user. See examples of ssti vulnerabilities,. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. You should also read this: Aviation Ppt Template
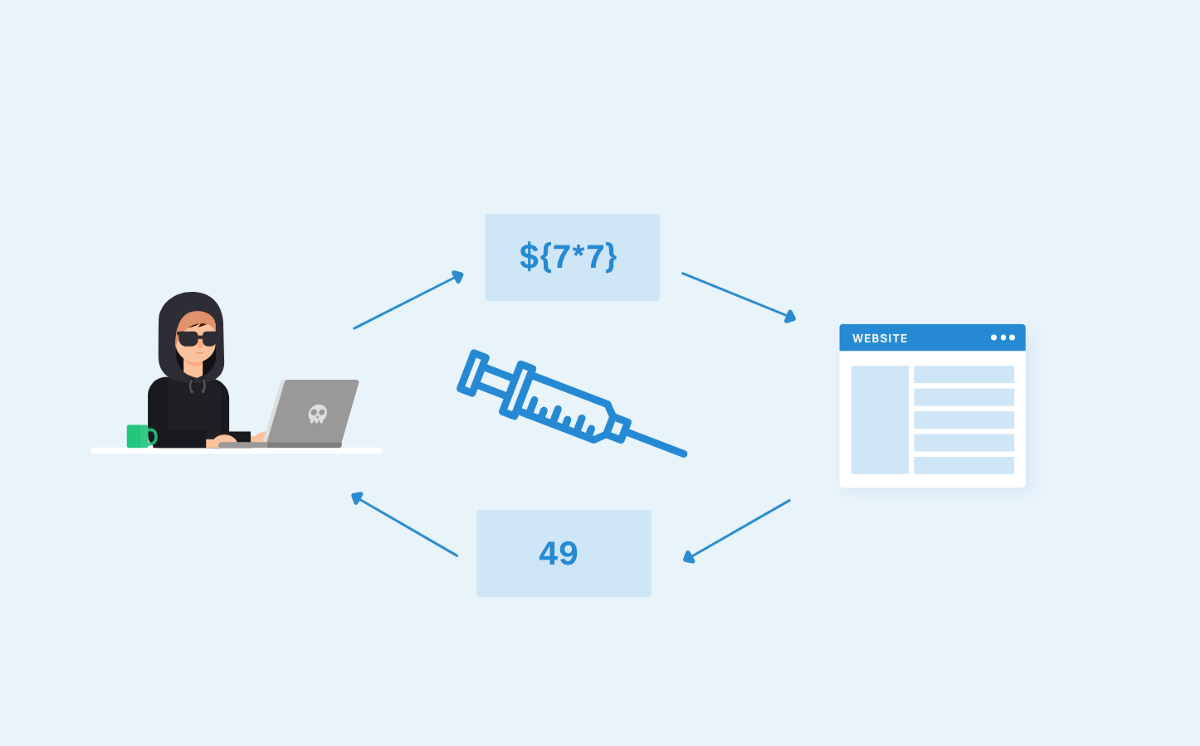
A Pentester’s Guide to Command Injection Cobalt - Understanding the mechanisms, risks, and. Find out how to identify, remediate, and prevent this vulnerability with examples and references. If an application improperly handles user. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. See examples of ssti vulnerabilities,. You should also read this: 2 Round Label Template 20 Per Sheet
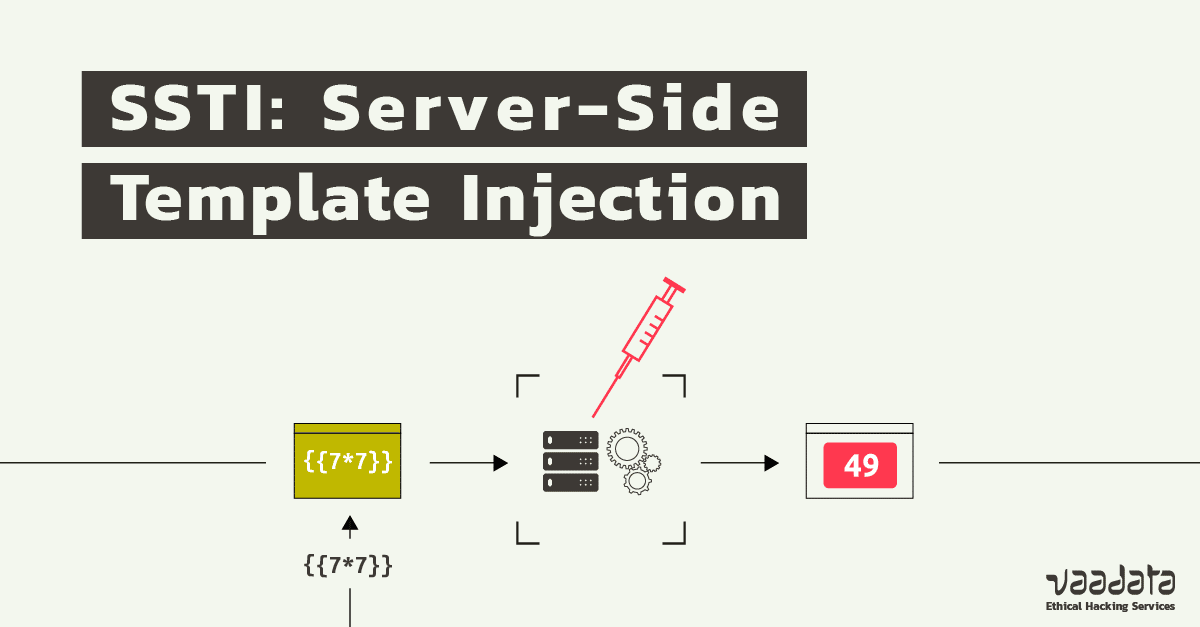
ServerSide Template Injection how to prevent it - See examples of ssti vulnerabilities,. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Understanding the mechanisms, risks, and. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. You should also read this: Daily Standup Template
Understanding ServerSide Template Injection (SSTI) and Its Role in Web - Understanding the mechanisms, risks, and. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. See examples of ssti vulnerabilities,. You should also read this: Care Home Care Plans Templates

Server Side Template Injection Explanation from the basics and a demo - See examples of ssti vulnerabilities,. Understanding the mechanisms, risks, and. Find out how to identify, remediate, and prevent this vulnerability with examples and references. If an application improperly handles user. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. You should also read this: Otf Tread 50 Template

SSTI ServerSide Template Injection Guide. • CyberAstral • Trusted - Find out how to identify, remediate, and prevent this vulnerability with examples and references. See examples of ssti vulnerabilities,. If an application improperly handles user. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Understanding the mechanisms, risks, and. You should also read this: Free Cleaning Business Price List Template